Beyond the DevSecOps Hype: The Journey Begins with Identity
Summary
This article delves into the critical role of Identity Management as the foundation for a successful DevSecOps strategy, arguing that without a deep understanding of identity, security efforts will fall short. I explore the historical evolution of identity from simple client-server models to complex distributed and cloud-based systems. A significant part of the discussion is dedicated to the three core domains of Identity Management: IAM (Identity and Access Management), PAM (Privileged Access Management), and IGA (Identity Governance and Administration). I highlight that while IAM is well-known, many companies struggle with PAM and IGA, despite their equal importance in securing critical resources and managing the entire identity lifecycle. The article also introduces the Zero Trust security model, emphasizing the “never trust, always verify” principle, which is crucial in today’s interconnected digital environment. My journey into demystifying security concepts highlights that mastering identity management is the true starting point for any effective DevSecOps implementation, far beyond relying solely on automated tooling.
Key Concepts
- DevSecOps Philosophy: Security is not just about tools; it requires deep understanding and proactive threat dissection.
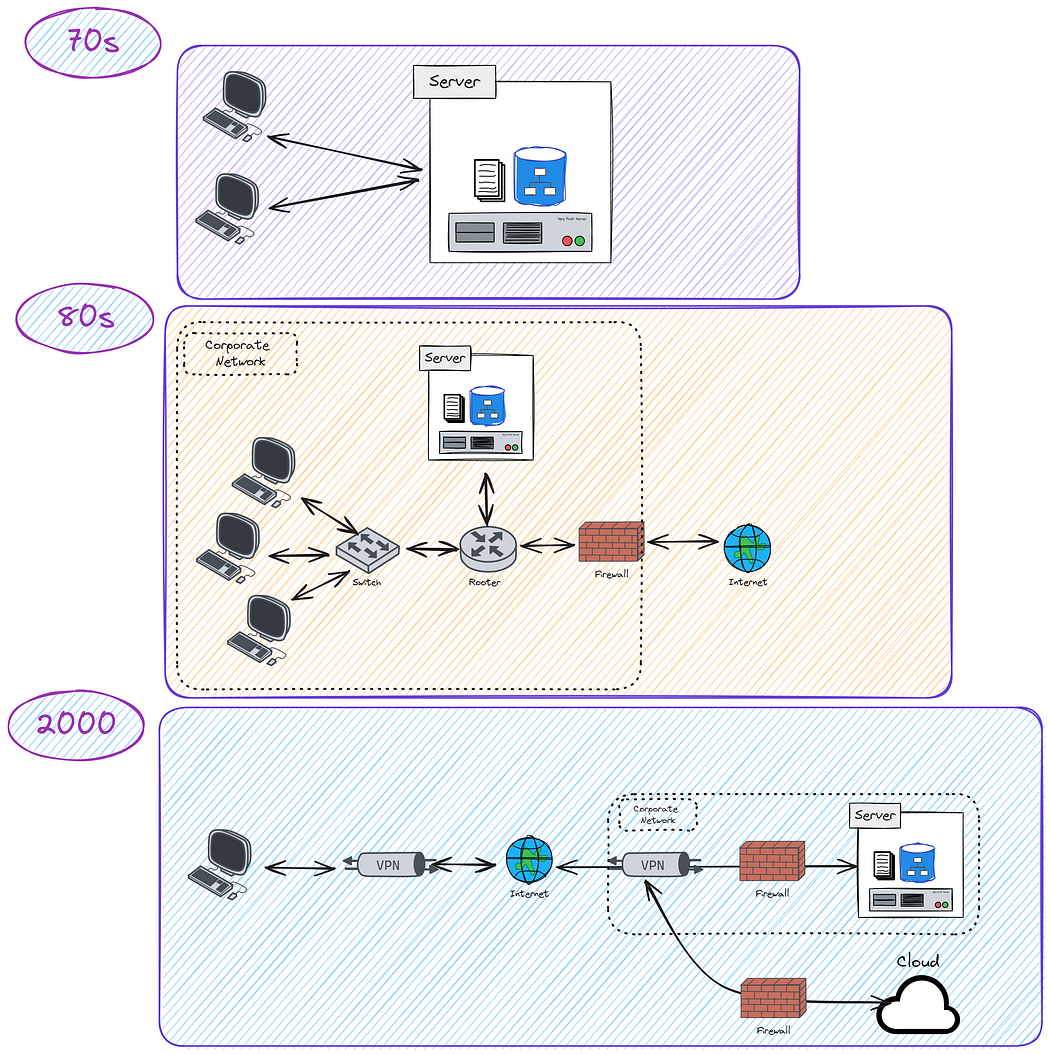
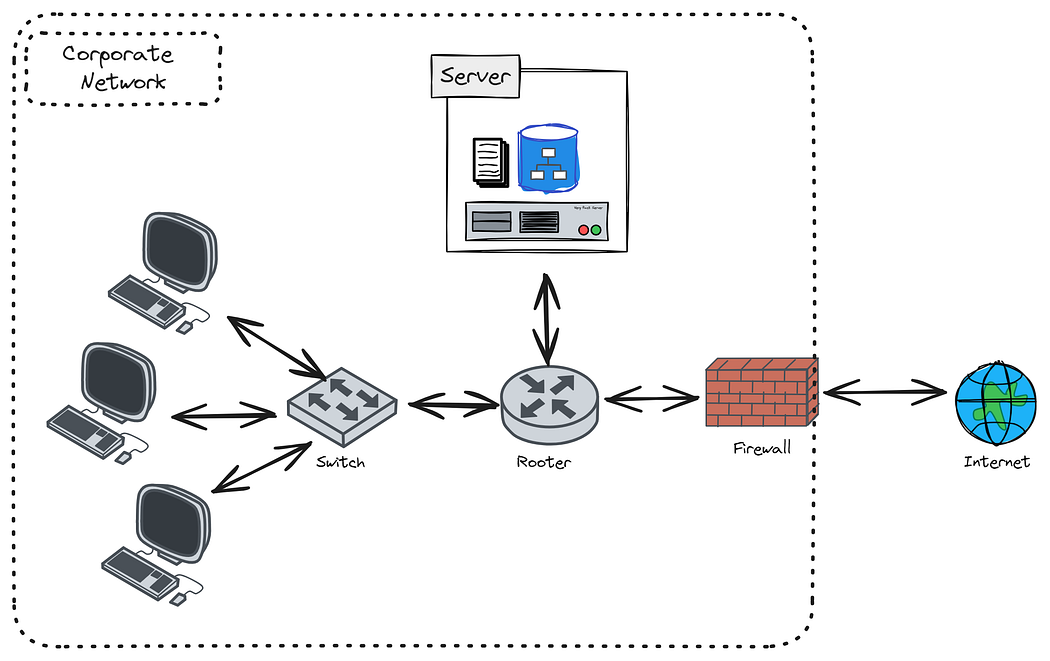
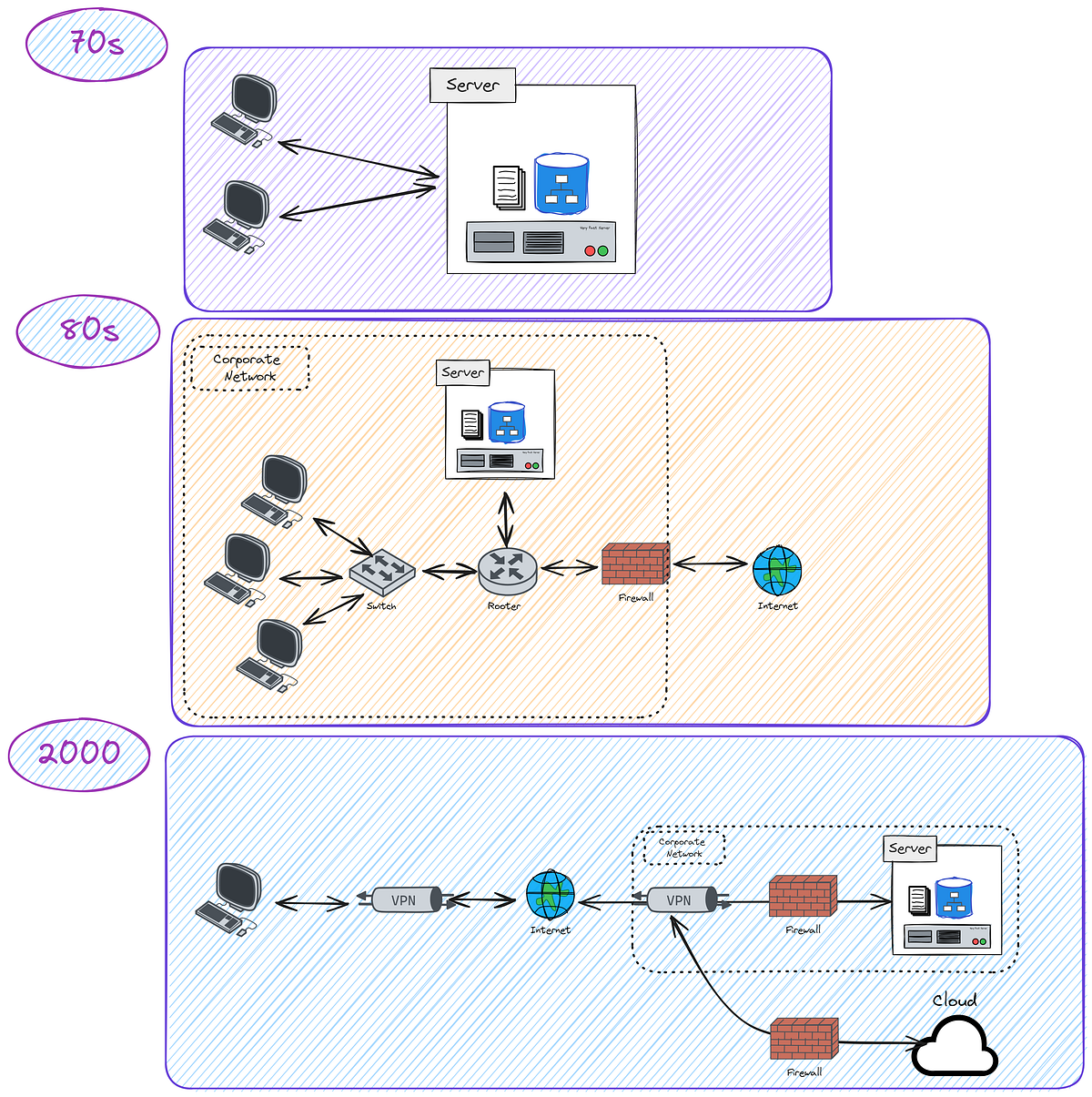
- Evolution of Identity: From early Client-Server models and Network Perimeter defenses to modern Distributed and Cloud-Based Systems, identity management has continuously adapted.
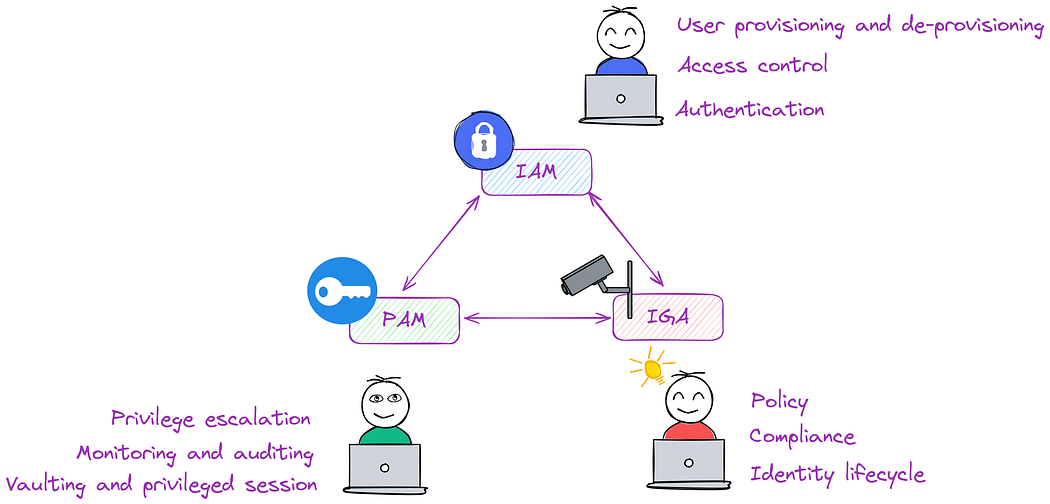
- Identity and Access Management (IAM): Focuses on user provisioning, access control, and strong authentication (e.g., MFA).
- Privileged Access Management (PAM): Manages accounts with elevated permissions, implementing least privilege, session management, and auditing. I believe this is one of the more challenging concepts for companies.
- Identity Governance and Administration (IGA): Establishes policies, ensures compliance, and streamlines the identity lifecycle from creation to deletion. This is also a concept I often see companies struggle with.
- Zero Trust: A paradigm shift “never trust, always verify,” continuously verifying access regardless of location, moving beyond traditional perimeter-based security.
References
Diagrams